Paranoia allows a user to securely transfer a text message by hiding it in a digital image file. 128 bit AES encryption is used to protect the content of the text message even if its presence were to be detected. Currently, no methods are known for breaking this kind of encryption within a reasonable period of time (i.e., a couple of years). Additionally, compression is used to maximize the space available in an image.
To send a message, a source text, an image in which the text should be embedded, and a key are needed. The key is used to aid in encryption and to decide where the information should be hidden in the image. Either another image or a short text can be used as a key. To receive a message, a source image containing the information and the corresponding key are both required. The result will appear in the text tab after decoding.
Two common Internet-friendly formats are offered. The algorithm for GIF images is a solid implementation of a tried and tested steganography technique, while the JPEG algorithm is more experimental. It is inherently more difficult to hide information in a JPEG image because that is exactly what the designers of JPEG wanted to avoid: the transmission of extra information that doesn't affect the appearance of the image.
Try it out:
- paranoia.jar
a JAR file containing the compiled program (HINT: Try java -jar paranoia.jar)
We used the waterfall software engineering method. These are the documents we submitted at each stage:
Please consult the Walk-through placed in the center of the main window for more help. The quality of the output images is dependent on the input images and the algorithm for the particular format. The following explains how to choose input images wisely such that encoding is successful and the output image does not look suspicious.
Hints for selecting GIF images:
- Medium to large digital photographs with lots of colors work well for the following reasons.
- One non-transparent pixel is needed to encode one bit of information, and the header is about 20 bytes. If the dimensions of a given image containing no transparent pixels are v by h pixels, then about (vh)/8 - 20 characters can be stored. For example, a 400 x 400 image can store roughly 19980 characters.
- Images should contain as many colors as possible. It is also best if many of the colors are similar. At least 4 colors are required.
Hints for selecting JPEG images:
- Large digital photographs generally work well for the following reasons.
- The images should have rather large dimensions. 64 pixels are needed to encode each bit of information, and the header is about 20 bytes. If the dimensions of a given image are v by h pixels, then about (vh/64)/8 - 20 characters can be stored. For example, a 400 x 400 image can store roughly 290 characters.
- Images should contain no large blocks of a single color. Otherwise, the embedded information may be visible to the human eye. For example, pebbles on a beach or a group of buildings in a city work well.
- Encoding may also cause an error for certain images. However, these images would generally not be used for steganography anyway. For example, images containing pure noise are mostly likely to cause problems, but few users enjoy viewing images containing white noise.

|
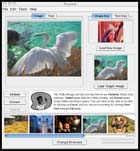
This is a full-size screen shot of the program. Studies have shown that typical users do not understand how encryption works. Thus, we tried to make our interface as easy to use as possible. Instead of worrying about troublesome public and private keys, the user simply uses another image as the key. |
And the credits go to...
| Subgroup | Developers |
|
|
|
| GUI | Gary Gong, Sheng Li, Jason Murray, Yuriy Shkolnikov |
| Security | Tam Le, Hiep Nguyen |
| JPEG | Edgar Berdahl, Joon Yul Lee |
| GIF | Sang Chung, Behrad Mozaffarian |